The 4-Minute Rule for Aws Backup
Some Known Details About Ec2 Backup
Table of ContentsWhat Does Aws Backup Mean?All about Ransomware ProtectionThe Of S3 BackupThe Facts About Aws Cloud Backup Revealed
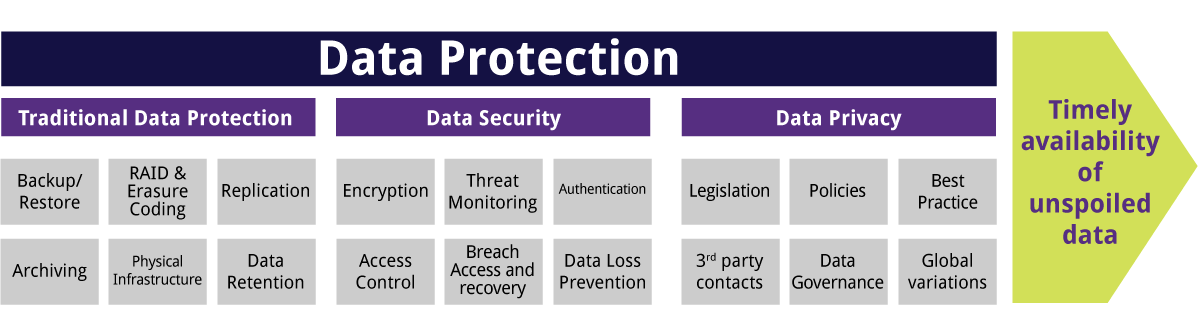
Information protection is the procedure of securing vital data from corruption, compromise or loss as well as providing the capability to bring back the information to a functional state must something take place to make the information inaccessible or pointless. Information security ensures that data is not corrupted, is obtainable for accredited objectives just, as well as remains in compliance with appropriate legal or regulative requirements (aws cloud backup).The range of information defense, nevertheless, goes beyond the idea of data availability as well as functionality to cover areas such as data immutability, conservation, and deletion/destruction. Roughly talking, data defense spans 3 wide categories, particularly, conventional information security (such as back-up as well as restore duplicates), information protection, and data privacy as displayed in the Figure listed below. Number: The 3 Classifications of Information Protection The principle of data security is to release methods and modern technologies to safeguard and also make data available under all situations. Storage technologies can be used to protect data by utilizing disk, tape or cloud backup to safely keep duplicates of the information that can be made use of in the occasion of data loss or interruption.
, transformed block monitoring, and so on,) are offering an additional layer of data security in addition to conventional backup.
The data storage space market looks at information protection generally from an innovation perspective in what is needed to keep information protect and offered. Information protection is specified by the European Union (EU) in a very various way as well as is frequently utilized where various other regions might make use of the term information personal privacy.
8 Easy Facts About S3 Backup Explained
Information goes to the center of company. https://www.leetchi.com/c/clumi0. For numerous companies, digital adoption drives approach. Data is necessary to meeting client needs, reacting to unexpected market shifts as well as unpredicted events. That's why information defense should get on your mind. Enterprises generate large quantities of information from multiple resources. The sheer quantity as well as information of venture data created throughout doing company needs ongoing interest to exactly how you secure and also keep it.
Today, it consists of Io, T devices and sensing units, industrial equipments, robotics, wearables and also even more. Information defense helps minimize threat and also allows a service or agency to respond rapidly to threats. Data security is essential because the overall number of computing devices boosts every year, as well as computing is currently much more complex.
The price of data development is outpacing mounted storage space, as well. In 2020, International Data Firm (IDC) reported 64 (https://snip.ly/zwufkk). 2 ZB of information was developed or duplicated. Researchers associate this dramatic rise to the globally demand for electronic services throughout the year. Not all information created in 2020 was kept, but IDC recommends there is ample evidence storing much more information could benefit ventures.
S3 Cloud Backup Can Be Fun For Anyone
The production market has a tendency to invest fewer sources in protecting commercial procedures modern technology (OT) than in their business networks. That leaves OT systems available to jeopardize. These OT systems include self-driving vehicles, robotics, Industrial Io, T tools and also sensing units. Essential infrastructure relies upon industrial control systems in addition to a great deal of different OT systems to function.
The manufacturing industry is a preferred strike target, also. In 2020, production, energy and health treatment sectors dealt with the highest possible rate of attack according to IBMs Yearly X-Force Risk Index. Securing corporate networks without offering the same focus to OT as well as equipment opens them for an attack. Digital possessions are rewarding targets, much more so as even more organizations resolve digital development initiatives linking much more solutions.
Data protection for supply chains and also third-party accessibility to systems is vital to shield them from cyberattacks. Balancing conformity with conference company purposes can be a challenge if you do not have a data defense method in place.
The order concentrates on activities to enhance cybersecurity with bringing critical framework as well as federal government networks up to modern requirements. This will only get more complicated as the government passes new legislations as well as even more carefully implements older guidelines - https://giphy.com/channel/clumi0.
Indicators on Data Protection You Need To Know
There More Info stay no sweeping government regulations on customer data personal privacy protections. Data defense and also data safety are comparable yet unique.
A detailed information safety technique safeguards electronic assets against attack while accounting for and securing against expert dangers. (These continue to be a leading cause of data violations yearly.) Deploying data safety devices and technologies offer businesses a means to analyze important data at its storage locations. They also help acquire understanding into just how individuals and tools are utilizing it.
